The following blog post summarizes my reasoning on how to deliver solutions that provide digitalization and how to stay secure and stay the course. My reasoning is mostly influenced by the Hyppönen Law, and by the latest trends in the software development world. The most important thing about security and digitalization is that they have to be aligned. Additionally, it is a continuous process and not a one-time checklist.
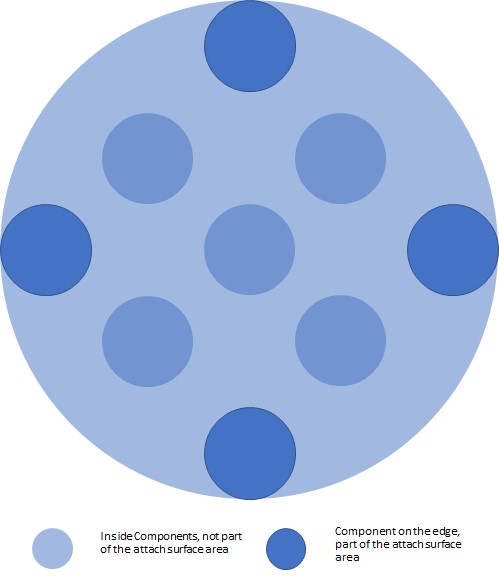
Minimize the Attack Surface Area
With the enabling technologies such as cloud, IoT, 5G, and mobile, the solutions we deliver become more powerful and bring more value. However, at the same time, they extend the cyberattack surface area. Adding a new component to a single solution means another component we must protect. Of course, one simple solution for this challenge is not extending the solutions and not benefiting from the enabling technologies. You can stop the digitalization right now and enjoy in your safe zones. However, if you stop the digitization, the competition will take over your market position because you are not offering what the market is expecting. Digitalization is an ongoing process, and more industries already benefit from the enabling technologies. In this story, there are two extreme cases: being completely locked and secure and completely open and insecure. If you are locked, the competition will provide better services. If you are to open, you are exposed to high risk. The winning solution lies between the two extreme cases—a solution with minimal attack surface that still benefits from the enabling technologies. At Nebb, we have the experience and know-how to provide our customers with the most optimal and functional solution. Providing minimal attack surface area happens in the design phase of the solution. We take a deep look at the non-functional requirements and provide a corresponding architecture with security as a top priority non-functional requirement.
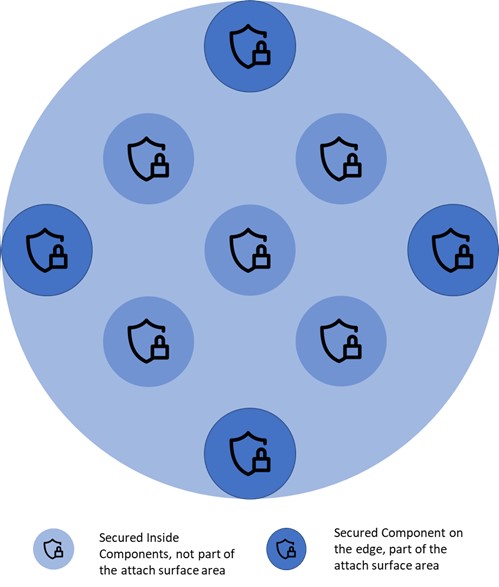
Security in Depth
Minimizing the attack surface is not enough. There are many examples of cyber-attacks where with social engineering, the attackers get easily inside the solutions (under protection). Therefore, the next step is to implement each component of the system and each component layer by following the latest security best practices. Since the system component can be implemented in different technologies like mobile devices, IoT devices, cloud, PLC, SCADA, our engineers have to excel at each technology stack. By isolating the components, even though they may not be part of the attack surface, we provide a solution with mitigated risk. If the attackers break the main defense, they still have to deal with the component defense.
Software Supply Chain Security
The design and development of a secure solution is one great challenge. Delivering the original solution to the customer is another challenge. There are many examples where the software supply chains were under attack. In such attacks, the original solutions are replaced with replicated solutions with an injected backdoor. Therefore, securing each step of the software supply chain is equally important. Namely, each step must validate that it addresses the original solution, not the injected. The supply chain for software solutions is getting more automated (DevOps), but also more reliable and with integrated security (DevSecOps.)